Web application firewall
A web application firewall (or WAF) filters, monitors, and blocks HTTP traffic to and from a web application. The difference between a WAF and a regular firewall lies in a WAF's ability to filter the content of specific web applications while regular firewalls serve as a safety gate between servers. By inspecting HTTP traffic, it can prevent attacks stemming from web application security flaws, such as SQL-injections, cross-site scripting (XSS), file inclusion, and security misconfigurations.
ModSecurity
ModSecurity, sometimes called Modsec, is an open-source web application firewall (WAF). Originally designed as a module for the Apache HTTP Server, it has evolved to provide an array of Hypertext Transfer Protocol request and response filtering capabilities along with other security features across a number of different platforms including Apache HTTP Server, Microsoft IIS and Nginx. It is a free software released under the Apache license 2.0.
The platform provides a rule configuration language known as 'SecRules' for real-time monitoring, logging, and filtering of HTTP communications based on user-defined rules.
Although not its only configuration, ModSecurity is most commonly deployed to provide protections against generic classes of vulnerabilities using the OWASP ModSecurity Core Rule Set (CRS). This is an open-source set of rules written in ModSecurity's SecRules language. The project is part of OWASP, the Open Web Application Security Project. Several other rule sets are also available.
To detect threats, the ModSecurity engine is deployed embedded within the webserver or as a proxy server in front of a web application. This allows the engine to scan incoming and outgoing HTTP communications to the endpoint. Dependent on the rule configuration the engine will decide how communications should be handled which includes the capability to pass, drop, redirect, return a given status code, execute a user script, and more.
How it works inside Roxy-WI
Roxy-WI allows installing, configure and manage WAF for NGINX. You integrate WAF with your NGINX service in a click.
Roxy-WI allows you select operating mode of ModSecurity.
ModSecurity works with default settings. Roxy-WI pre-installs OWASP-CRS rules with default settings. If you want to change any parameters you should edit them. All parameters are stored in the following directory: /etc/nginx/waf/rules/
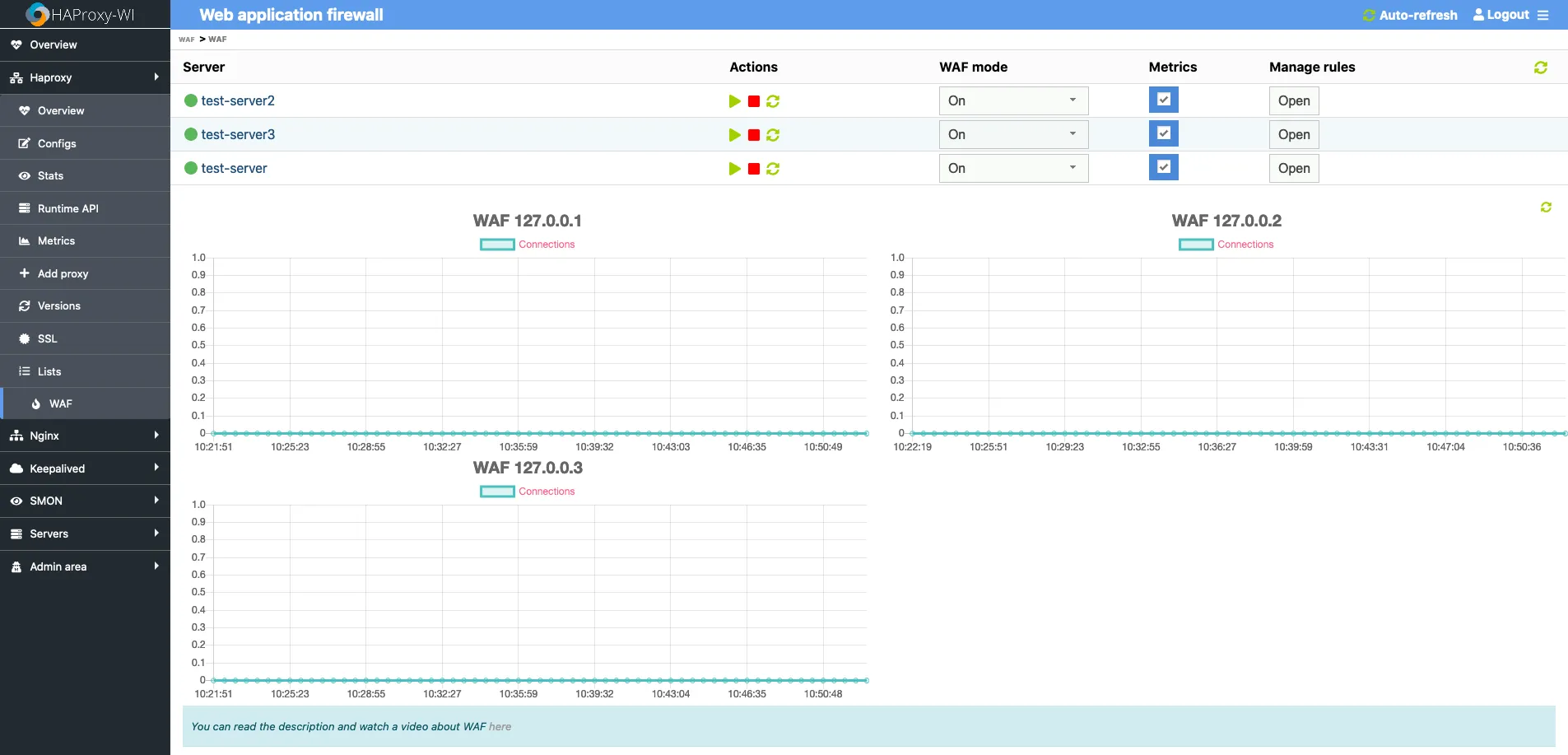
Roxy-WI add into a nginx.conf settings which enable ModSecurity globally, but keeps it in "off" state by default. If you would like to enable it, just press the "start" button on the WAF page for needed server.
If you want to enable it only for a few domains, you have to add the following settings to a config file. For instance to conf.d/example.com.conf
Since 6.1.3 version you can edit the rules or create a new one. Be aware: a rule file syncs from a Master server to a Slave, but you should to add a rule with the same name on the Slave server, after creating the rule on the Slave server you can manage it via Roxy-WI.
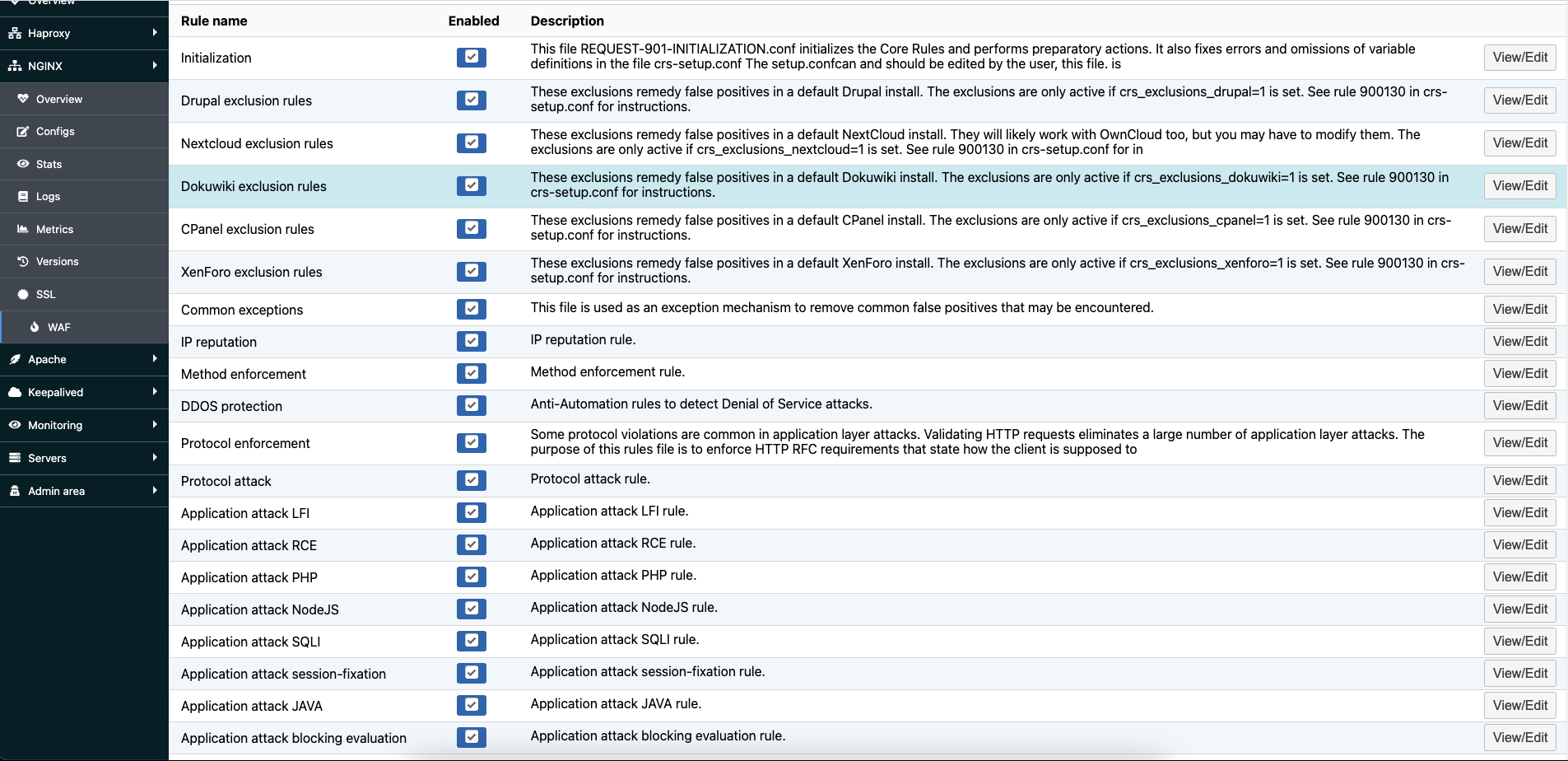
The default OWASP-CRS rules
Roxy-WI pre-installs the following rules by default:
You can disable or enable rules via Roxy-WI by setting or unsetting the Enabled checkbox. Do not forget to reload the Nginx after modifying the rules.
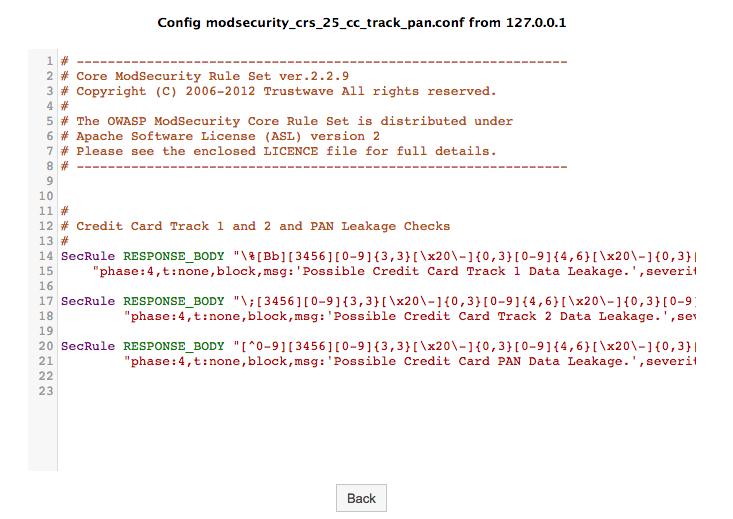
You can view the details of each rule by pressing the View button. Rules look as shown below: