A web application firewall (WAF) is designed to filter, monitor, and block HTTP traffic to and from a web application. Unlike traditional firewalls, which act as a safety barrier between servers, a WAF specifically focuses on the content of individual web applications. By inspecting HTTP traffic, a WAF can effectively prevent attacks that exploit web application security vulnerabilities, including SQL injection, cross-site scripting (XSS), file inclusion, and security misconfigurations.
ModSecurity, often referred to as Modsec, is an open-source web application firewall (WAF) initially developed as a module for the Apache HTTP Server. It has since evolved to offer a comprehensive suite of Hypertext Transfer Protocol (HTTP) request and response filtering capabilities, along with various security features, across multiple platforms, including Apache HTTP Server, Microsoft IIS, and NGINX. ModSecurity is free software released under the Apache License 2.0.
The platform includes a rule configuration language known as SecRules, which enables real-time monitoring, logging, and filtering of HTTP communications based on user-defined rules.
ModSecurity is commonly deployed to protect against a wide range of vulnerabilities using the OWASP ModSecurity Core Rule Set (CRS). This open-source collection of rules is written in ModSecurity's SecRules language and is part of the Open Web Application Security Project (OWASP). In addition to the CRS, several other rule sets are also available.
To detect threats, the ModSecurity engine can be embedded within the web server or configured as a proxy server in front of a web application. This setup allows the engine to scan both incoming and outgoing HTTP communications. Depending on the rule configuration, the engine determines how to handle these communications, with options to pass, drop, redirect, return a specific status code, execute a user script, and more.
You can install, configure, and manage WAF for HAProxy in the HAProxy => WAF section.
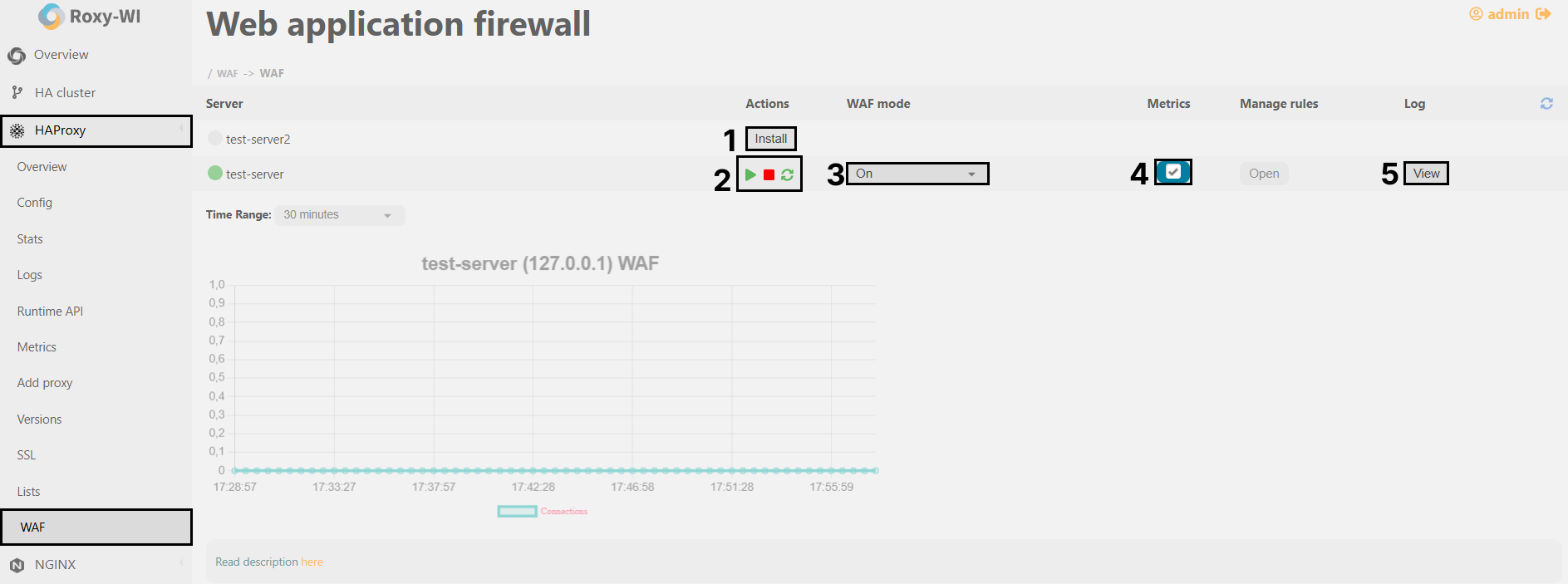
1. To install the WAF service, click Install.
2. To start/stop/restart the WAF service, click the appropriate button.
3. To select the WAF mode, choose an option from the drop-down list.
4. To collect WAF connections metrics, check the Metrics box.
5. To view WAF logs, click View.
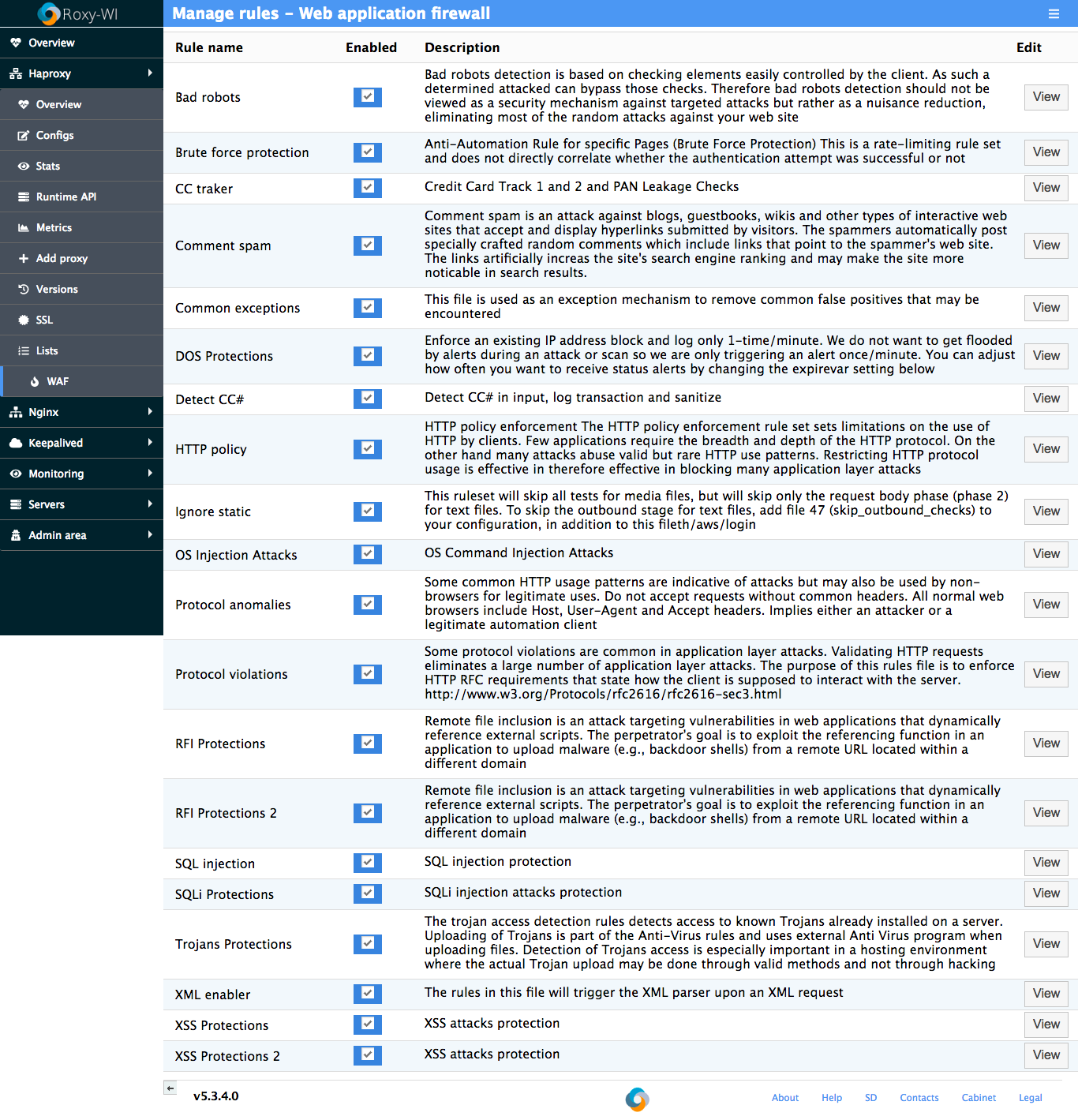
Roxy-WI comes with OWASP-CRS rules pre-installed using default settings. If you need to modify any parameters, you can do so by editing them. All parameters are stored in the following directory: /etc/haproxy/waf/rules/
Roxy-WI pre-installs a set of rules by default. Click Open in the Manage rules column to view the full list of rules.
To enable or disable specific rules, check the Enabled box. Remember to restart WAF after making any changes.
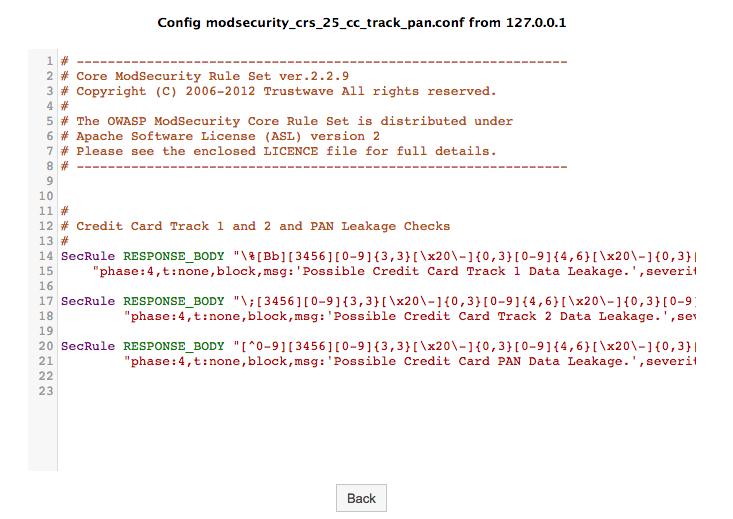
You can view the details of each rule by clicking the View/Edit button. The rules will be displayed as shown below:
You can install, configure, and manage WAF for NGINX in the NGINX => WAF section.
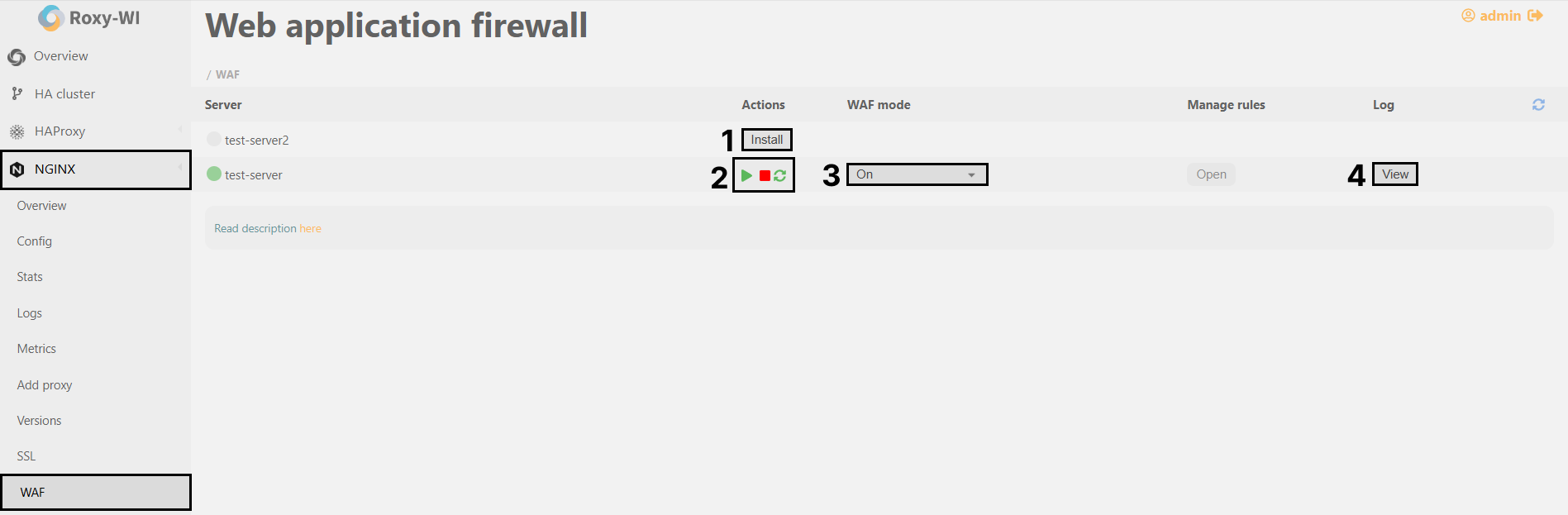
1. To install the WAF service, click Install.
2. To start/stop/restart the WAF service, click the appropriate button.
3. To select the WAF mode, choose an option from the drop-down list.
4. To view WAF logs, click View.
Roxy-WI comes with OWASP-CRS rules pre-installed using default settings. If you need to modify any parameters, you can do so by editing them. All parameters are stored in the following directory: /etc/nginx/waf/rules/
Roxy-WI also adds configuration data to the nginx.conf file and enables ModSecurity globally, but it is set to "off" by default. To enable ModSecurity, click start on the WAF page.
If you want to enable ModSecurity for specific domains only, you will need to add the following settings to a configuration file (e.g. conf.d/example.com.conf):
Roxy-WI pre-installs a set of rules by default. Click Open in the Manage rules column to view the full list of rules.
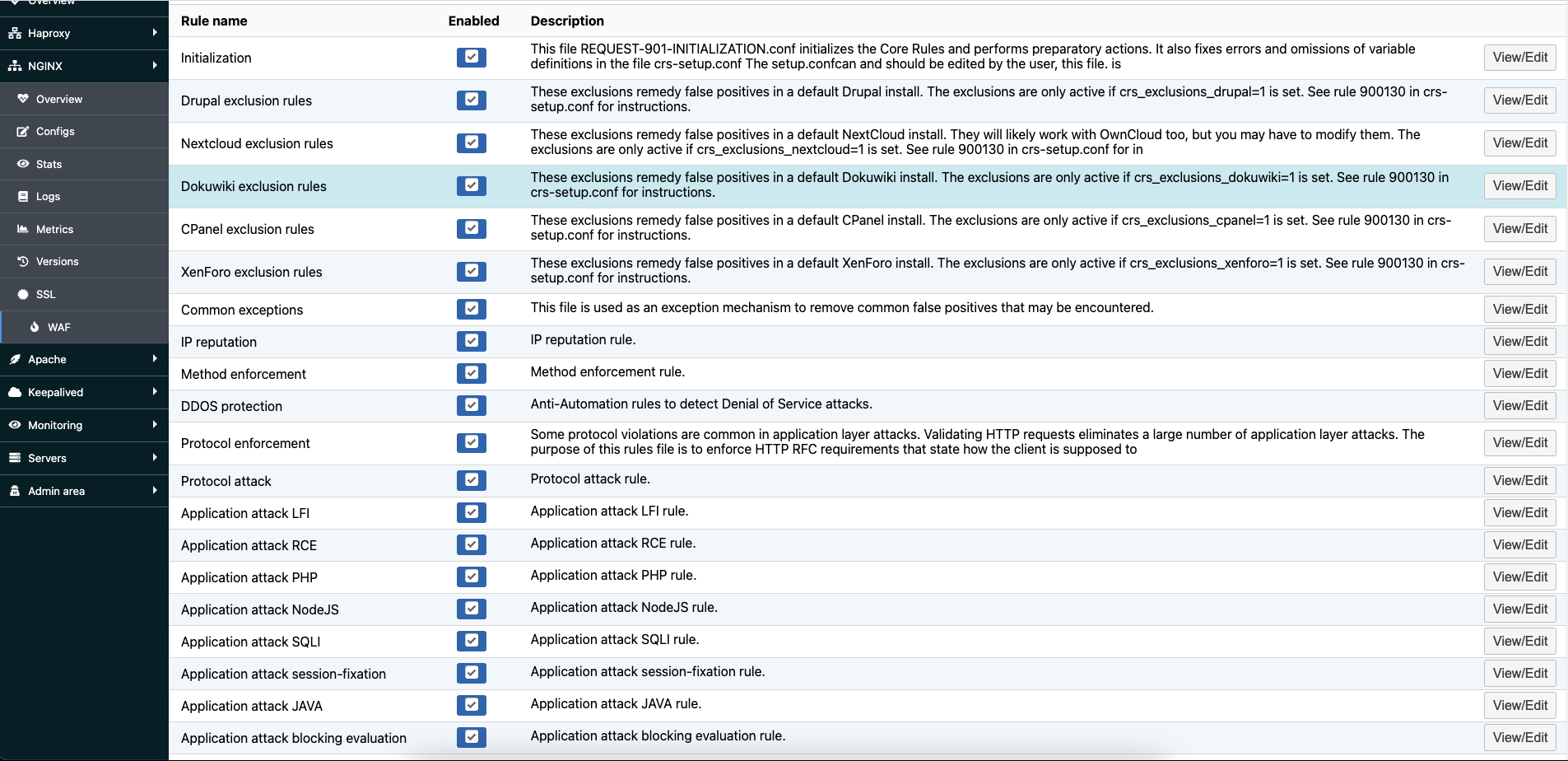
To enable or disable specific rules, check the Enabled box. Remember to restart WAF after making any changes.
You can view the details of each rule by clicking the View/Edit button. The rules will be displayed as shown below: